News
Drones and the (Potential) Defense Techniques Against Cyber Attacks
If you have been reading about the dangers of cyber attacks for computers, you will probably be surprised to hear that these forms of attacks are increasingly popular and aiming a new category of technology – unmanned aerial vehicles (UAVs) or also known as drones.
In a review paper titled, “Defense Techniques Against Cyber Attacks on Unmanned Aerial Vehicles”, and written by Charan-Gudla, Shohel Rana and Andrew H. Sung of the School of Computing Sciences and Computer Engineering, The University of Southern Mississippi, the topic of defense techniques is being explored, mainly because of the growing potential of drones and their importance in today’s society.
Moving Target Defense (MTD) Techniques in Drones
The paper also proposes to study the Moving Target Defense (MTD) and the techniques associated with it – mainly as a way to prevent cyber attacks and reduce the dangers while increasing the difficulty of attacking drones and harming them through this (common) technique.
As an example, the authors show an illustration of a well-known cyberattack that is performed on a popular commercial drone – describing their findings in regards to the damages, vulnerabilities and defense techniques to prevent such attacks.
Even though drones nowadays offer many advantages, they are prone to various physical and cyber attacks. The common forms of communication include sending and receiving data such as Satellite, Cellular, Wi-Fi, GPS, ZigBee.
When it comes to the potential cyberattacks, the authors point out to the 2009 case where Iraqi insurgents hacked predator drone feeds – as well as the case in 2011, when a computer virus has infected networks used by pilots controlling US air force drones at Creech air force base in Nevada. Aside from these, the authors outline a few additional cases of cyber attacks enforced on drones.
The paper discusses various vulnerabilities of UAVs and the hacking techniques which are further explored in the sections below.
Common Cyber Hacking Techniques When Targeting Drones
The main hacking techniques which target drones and mean to attack their systems include:
- Data packet capture – a cyber attack that gathers the required information about the target by a data packet capture method, where the wireless network of the drone sends out the beacons frames which can be easily captured.
- Denial of Service attack (DoS) – This common type of attack also includes drones, mainly through continuous de-authentication requests which are being sent to the targeted access point, exhausting its memory.
- Man-in-the-middle attack – Here, the attacker spoofs and gains control over the communication network between the drone and the remote control (RC) device user, gathering data from the drone as if he is the original RC user.
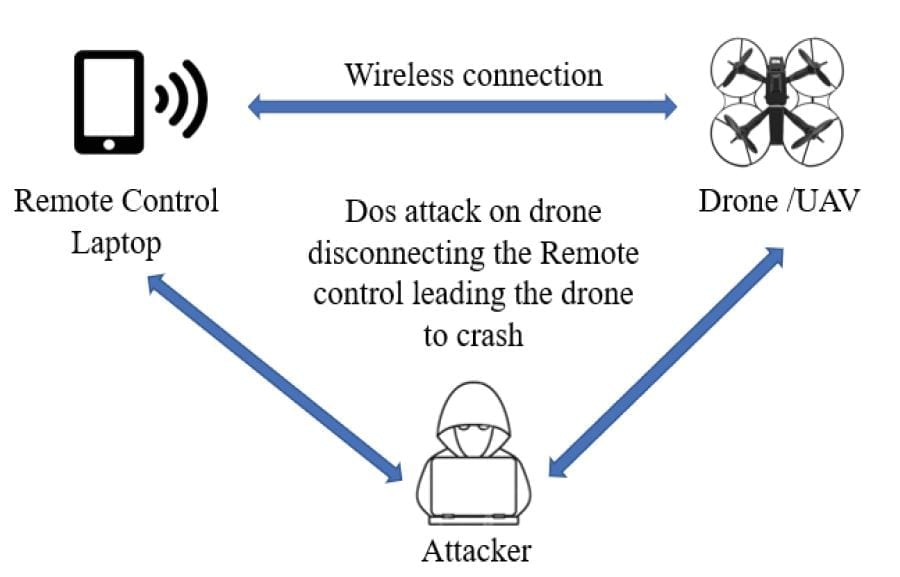
Denial of Service (DoS) attack
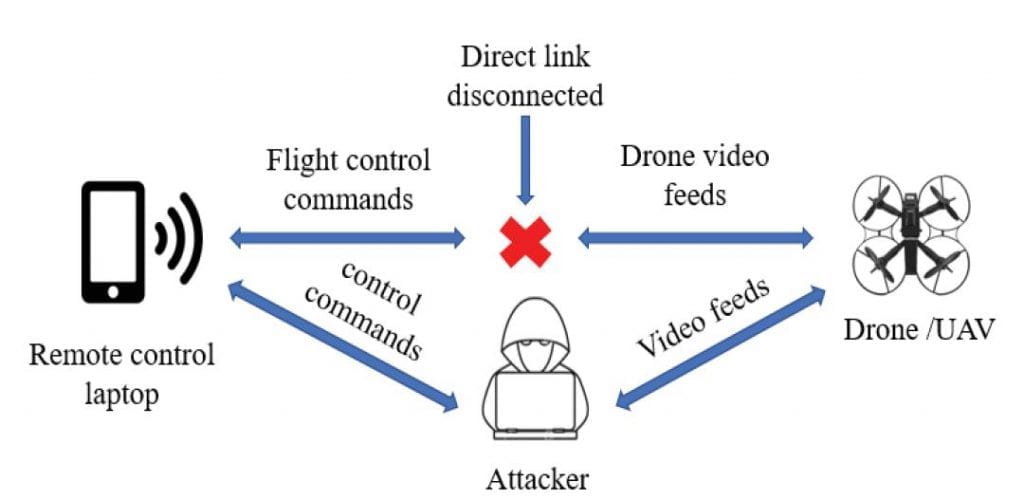
Man-in-the-Middle Attack
DoS seems to be one of the most popular hacking techniques that is (quite easily) implemented on a drone’s static network.
The Actual Defense Against Cyber Attacks Like These
What’s more important for every reader of this paper is the actual defense practices that drones need to establish against attacks like these. As the paper mentions, there are three potential defense techniques that can be used, including:
- Wireless network encryption – Here, the AR drone will act as an access point and its network is unencrypted and open, multiple devices can be connected to it but only device can control it. The wireless network needs to be encrypted with a WPA2 security.
- Intrusion detection system (IDS) – IDS are kind of defensive tools but doesn’t provide preventive actions against the attacks. It’s usually a software which monitors the network behavior and notify if there are any anomalies.
- Moving target defense (MTD) – Moving Target Defense [26] is a technique where system characteristics are changed from static to dynamic, thus increasing the complexity for the hacker to attack.
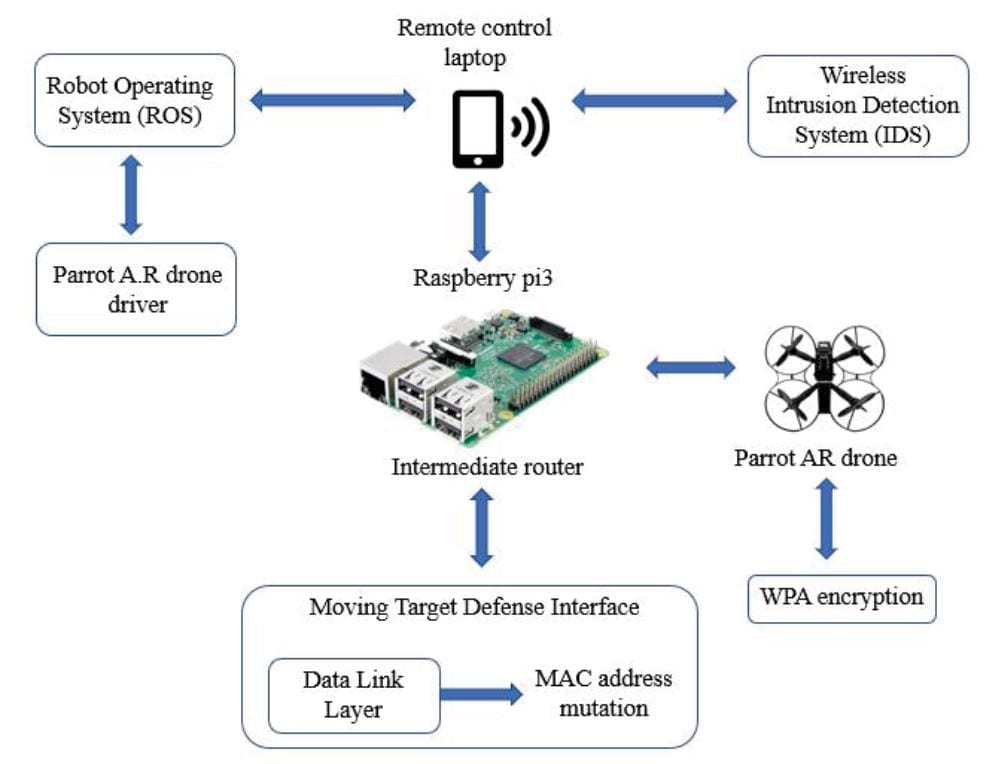
Base station control system model
When summing up the results of the attacks and the defense practices, the authors show the implementation of the defense techniques against cyber-attacks on parrot AR drone wireless network.
As the tests show, the commercial, civilian as well as military applications of UAVs are increasing rapidly – which is why every drone system deserves a solid defense framework – especially in times when drones carry important information, photos, video feeds, payloads etc.
Citation: Gudla, Charan & Rana, Md & Sung, Andrew. (2018). Defense Techniques Against Cyber Attacks on Unmanned Aerial Vehicles. Int’l Conf. Embedded Systems, Cyber-physical Systems, & Applications | ESCS’18 – https://www.researchgate.net/publication/328135272_Defense_Techniques_Against_Cyber_Attacks_on_Unmanned_Aerial_Vehicles
How useful was this post?
Click on a star to rate it!
Average rating 0 / 5. Vote count: 0
No votes so far! Be the first to rate this post.
We are sorry that this post was not useful for you!
Let us improve this post!
Tell us how we can improve this post?